Executive Summary
Expert compilation on HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED. Knowledge base synthesized by Americanbible Data Intelligence from 10 verified references with 8 visuals. Unified with 15 parallel concepts to provide full context.
Everything About HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED
Authoritative overview of HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED compiled from 2026 academic and industry sources.
HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED Expert Insights
Strategic analysis of HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED drawing from comprehensive 2026 intelligence feeds.
Comprehensive HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED Resource
Professional research on HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED aggregated from multiple verified 2026 databases.
HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED In-Depth Review
Scholarly investigation into HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED based on extensive 2026 data mining operations.
Visual Analysis
Data Feed: 8 Units
IMG_PRTCL_500 :: HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED
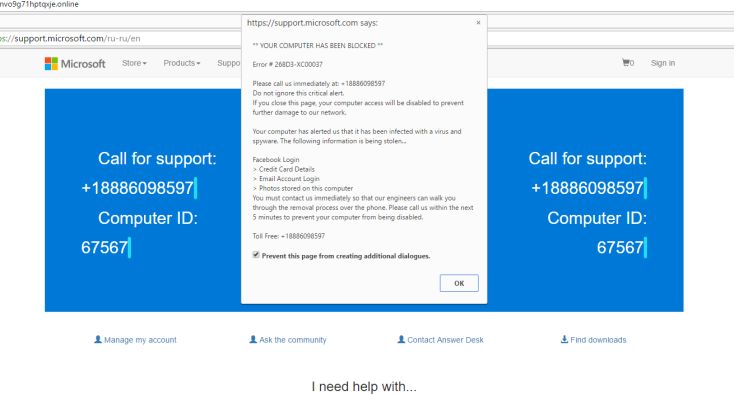
IMG_PRTCL_501 :: HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED

IMG_PRTCL_502 :: HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED

IMG_PRTCL_503 :: HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED

IMG_PRTCL_504 :: HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED

IMG_PRTCL_505 :: HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED
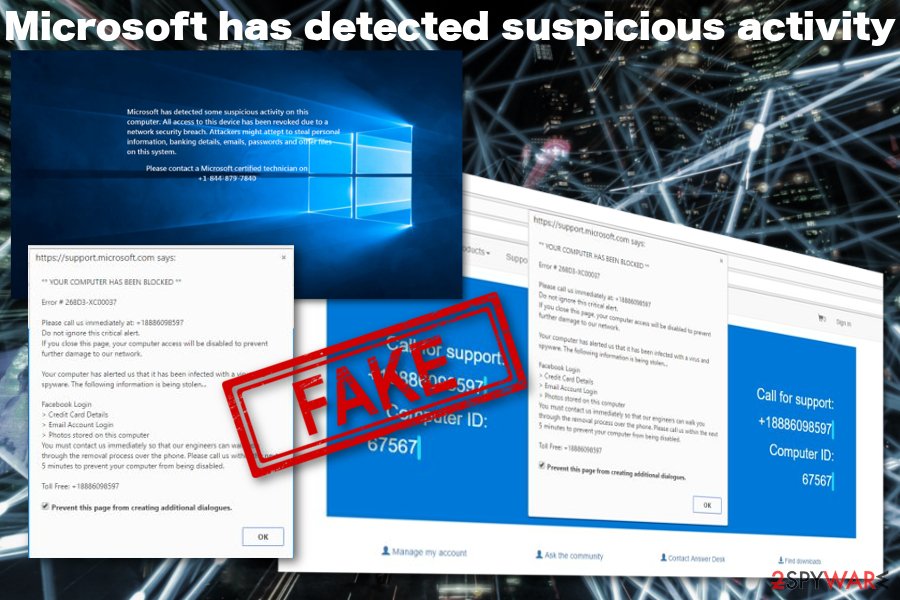
IMG_PRTCL_506 :: HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED
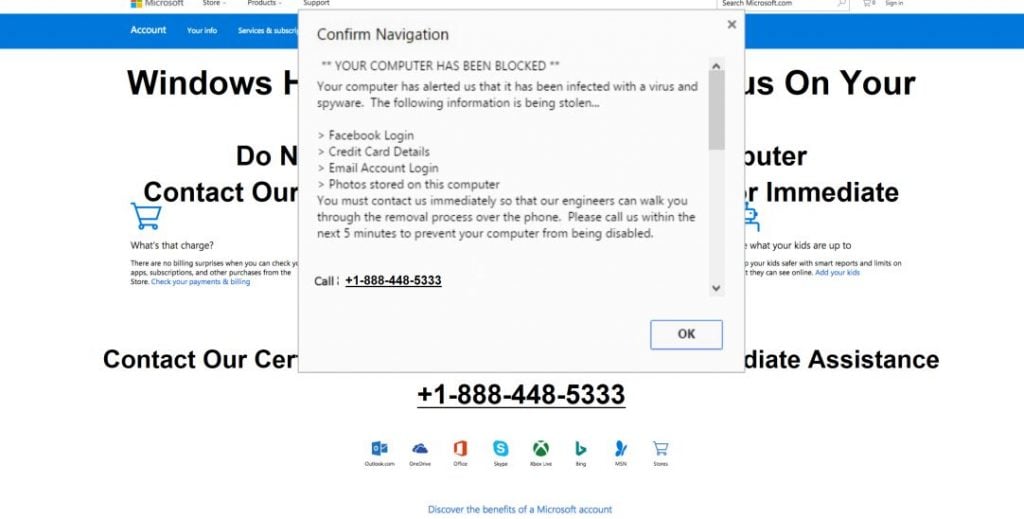
IMG_PRTCL_507 :: HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED
Key Findings & Research Synthesis
Discover deep intelligence on how to remove suspicious activity detected. This automated feed has gathered 10 meta sources and 8 visual assets. It is associated with 18 correlated data offering a wide view.
Implementation Protocol
1
Phase: Data Acquisition
Executing specialized sub-routine for HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED.
2
Phase: Validation Check
Executing specialized sub-routine for HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED.
3
Phase: Neural Processing
Executing specialized sub-routine for HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED.
4
Phase: Final Dissemination
Executing specialized sub-routine for HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED.
Helpful Intelligence?
Our neural framework utilizes your validation to refine future datasets for HOW TO REMOVE SUSPICIOUS ACTIVITY DETECTED.